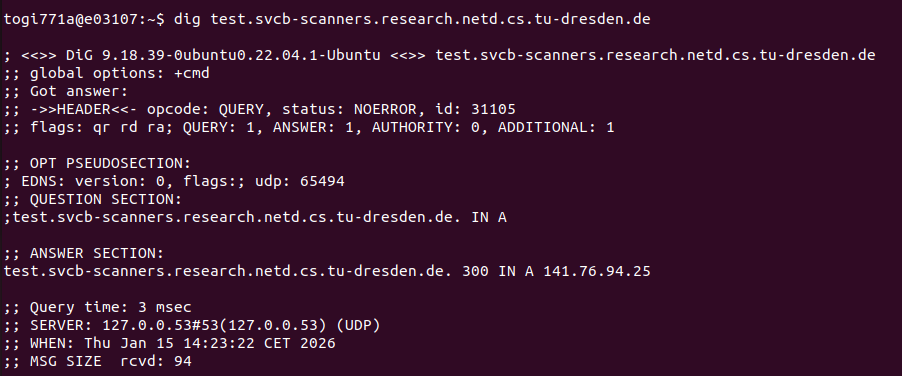
test.svcb-scanners.research.netd.cs.tu-dresden.de using an external resolver, confirming successful delegation.
Project status: First measurements
Author: Tomasz Danek-Giemza
This project investigates whether and how Internet scanners interact with modern DNS records such as SVCB/HTTPS and SRV. We deploy an authoritative DNS infrastructure and observe scanner behavior under controlled changes to DNS records. The focus lies on protocol parameters (e.g., HTTP/1.1, HTTP/2, HTTP/3) and their impact on subsequent network activity, including TCP and UDP traffic. Packet-level measurements are used to correlate DNS queries with transport-layer behavior.
With the introduction of SVCB and HTTPS DNS records, service discovery and protocol negotiation increasingly move into the DNS layer. While client behavior for these records is well specified, little is known about how Internet-wide scanners react to such signals. Understanding whether scanners query, interpret, or act upon SVCB and SRV records provides insight into their capabilities and assumptions. This project aims to empirically study scanner behavior by operating a controlled authoritative DNS setup and incrementally modifying DNS records.
The measurement infrastructure consists of a single virtual machine hosted within the university network. The VM is equipped with a public IPv4 address range and is directly reachable from the Internet.
141.76.94.25/26141.76.94.26/26The setup intentionally uses a minimal infrastructure in order to keep external influences low and ensure full control over configuration changes.
The delegated domain is served by an authoritative DNS server operated on the measurement VM. PowerDNS is configured in authoritative-only mode and does not provide recursive resolution. This ensures that all observed DNS traffic is directly related to the operated zone and not influenced by resolver-side behavior.
Two authoritative nameservers are configured for the zone and mapped to two distinct IPv4 addresses. Both addresses terminate on the same virtual machine. While this setup does not provide redundancy in the classical sense, it enables controlled observation of scanner behavior in the presence of multiple authoritative nameservers.
All DNS records are managed explicitly within the zone file, allowing precise control over record types, parameters, and timing of changes during the measurement phases.
The virtual machine is configured with two public IPv4 addresses bound to a single network interface. Both addresses are permanently assigned via a persistent netplan configuration.
The authoritative DNS server is configured to listen on both addresses, enabling direct comparison of incoming traffic per address. This setup allows the measurement of scanner behavior towards multiple nameserver endpoints while keeping the underlying system and services identical.
No additional network filtering or rate limiting is applied at this stage, ensuring that all incoming traffic reaches the measurement infrastructure unmodified.
Before introducing experimental DNS records, the baseline setup was verified to ensure correct operation of all components. The verification steps and their outputs are documented below.
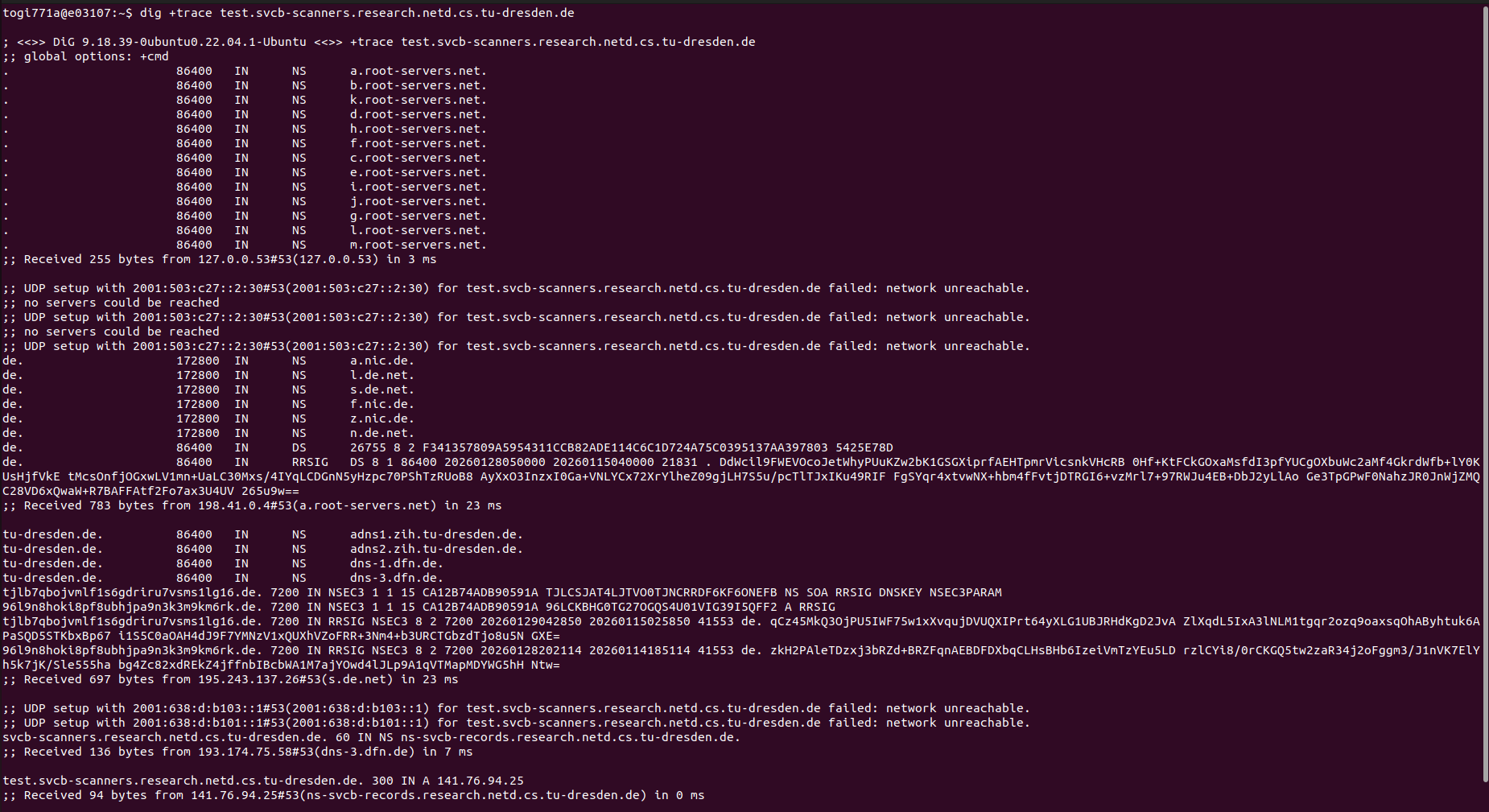
DNS resolution of test hostnames was verified using external resolvers, confirming that the delegated zone is reachable. The authoritative nature of the responses was additionally confirmed using trace-based DNS queries.

test.svcb-scanners.research.netd.cs.tu-dresden.de using an external resolver, confirming successful delegation.
HTTP connectivity was validated by accessing the hosted documentation page via the delegated domain. Packet capture functionality was tested using dumpcap by triggering controlled HTTP requests and verifying that corresponding network packets were recorded.
The measurement methodology follows an incremental approach. A verified baseline without experimental DNS records is established first. Subsequent experiments introduce individual DNS record changes while keeping all other parameters constant.
For each configuration, DNS query traffic and subsequent network activity are captured and analyzed. This allows attributing observed changes in scanner behavior to specific DNS record properties.
As a first experimental step, Service Binding (SVCB) records without any service parameters were introduced. This setup isolates the effect of the mere presence of SVCB records from any protocol negotiation or transport-layer behavior.
Two SVCB-enabled hostnames were deployed, each mapped to a different authoritative nameserver address. Both records point to functional HTTP services, ensuring normal fallback behavior for clients that do not interpret SVCB records.
During this phase, packet captures are performed continuously to observe DNS query behavior. No changes to DNS records or services are applied while the capture is active.
After a period of roughly one hour of packet capture the results were saved and evaluated. The show, that...